Top 10 Cybersecurity Facts & Stats in 2026

HighSpeedOptions prides itself on providing honest, quality content. While we may be compensated when you make a purchase through links on our site, all opinions are our own. Here's how we make money.
Table of Contents
It’s just a fact: if you use the internet, you are vulnerable to many types of cybercrimes. It doesn’t matter who your internet service provider is or the type of internet connection.
And to compound the issue, technology and cybercrime go hand in hand–as the number of devices connected to the internet increases, so does cybercrime.
Cybercrime causes trillions of dollars in damages and devastates individuals and businesses around the world each year. And it shows no signs of slowing down. In fact, according to this Gallup Poll, Americans now worry more about suffering a cyber-attack than they do about being a victim of a violent crime.
No matter your internet lifestyle, you need to be aware of potential online threats and security weaknesses. Check out these 10 cybersecurity statistics; from user error to data breaches, you’ll learn how widespread cybercrime really is and which online traps to avoid at all costs.
Many providers include internet security in their services, helping to keep you and your family safe from many cybersecurity threats.

Key Findings
- 68% of cyber breaches involve human error
- 15% of breaches stem from phishing emails
- Weak passwords contribute to ~30% of global data breaches
- 85% of cyberattacks are financially motivated
- 23% of smartphones have at least one high-risk or sideloaded app installed
- Over 8 million DDoS attacks were observed in the first half of 2025 alone
- Connected IoT devices are projected to reach ~20B in 2025 and 40B by 2030
- DDoS attacks estimated to hit 16 million globally by the end of 2025
- VPN adoption is growing — about 1 in 3 U.S. users (32%) now use a VPN
- Global cybercrime costs are projected to hit $10.5 trillion annually by 2025

1. Human error accounts for 68% of all cyber breaches
According to Verizon’s 2024 Data Breach Investigations Report, 68% of all successful cyber breaches are caused by human error. The most common errors people make include using weak passwords or accidentally sending sensitive data to the wrong person. After these, poor update hygiene, downloading and using unverified apps are common human errors.
Why it matters for you: Even a simple mistake like misaddressing an email or reusing a password can put your personal accounts or work data at risk.
How to Reduce Human Error in Cyberattacks
Double-check recipients. Before sending sensitive information, verify the email address or phone number.
Slow down under pressure. Phishing often works by creating urgency. Take a moment to verify before acting.
Report suspicious activity. If you notice a suspicious email or login attempt, report it to IT/security immediately.
A good rule of thumb: If you weren’t expecting it, don’t click it. Whether it’s a link, an attachment, or a request for information, pause and verify through another trusted channel before taking action.

2. Many successful cyber attacks stem from phishing emails
Phishing emails are the source of about 15% of all cyberattacks or breaches. The Anti-Phishing Work Group observed over a million phishing attacks in Q1 2025, the largest since 2023. And KnowBe4 reports a 17% increase in phishing emails between September 2024 and February 2025.
Disguised as someone you may know, phishing emails try to trick users into downloading malware attachments or entering passwords
Why it matters for you: Phishing scams are designed to trick you — not your IT team — meaning your inbox is often the first line of defense..
How to Identify Phishing Emails
Suspicious sender address. The display name looks familiar, but the actual email address is slightly off (extra letters, wrong domain, strange characters).
Generic greeting. “Dear Customer” or “Hello User” instead of using your real name.
Urgency or scare tactics. Phrases like “Act now,” “Immediate action required,” or threats of account suspension.
Mismatched URLs. Hover over a link: does the address match the supposed sender’s domain? If not, it’s likely a phishing attempt.
Unusual requests for sensitive info. Legitimate companies rarely ask for passwords, banking details, or verification codes via email.
A good rule of thumb: If something feels off, don’t click. Instead, go directly to the company’s official website or app to verify.

3. Weak passwords make up 30% of global data breaches
Weak passwords cause about a third of the world’s data breaches. It’s easy to fall into the habit of creating weak, more memorable passwords given how often various devices, apps, and websites prompt for password changes. It doesn’t help that, according to NordPass, some of the most common passwords still used today include 123456, password, and admin.
Why it matters for you: If you’re still using short or repeated passwords, a hacker could access multiple accounts with one stolen login.
Tips for More Secure Passwords
Avoid personal info. Don’t use names, birthdays, addresses, or common words that attackers can easily guess.
Use passphrases. Combine random words into a memorable phrase (e.g., “PurpleDog!Runs4Coffee$Moon”).
A Good Rule of Thumb: If you can easily remember it, it’s probably too weak — let a password manager do the remembering.

4. 85% of all cybersecurity attacks are financially motivated
According to Verizon’s 2025 DBIR report, the number one motivator for all cybersecurity attacks in the world is money (85%). With online banking and digital wallets increasing in popularity, the internet is ripe for financially motivated hackers. This means the need for cybersecurity and strong password protection is crucial for users. Internet service providers like Earthlink offer solutions to help secure your internet connection from the get-go.
Why it matters for you: Most attacks target money — from draining bank accounts to stealing credit card info — making your finances a prime target.
Tips to Reduce Financially Motivated Cyber Attacks
Verify payment requests. Always double-check invoices, wire transfers, or requests for funds — especially if they involve urgency or a change in account details.
Stay alert to phishing. Be cautious with emails or texts asking for login details, account resets, or financial info. Hover over links before clicking.
Monitor accounts regularly. Set up alerts on bank and credit card accounts to catch unusual transactions quickly.
A good rule of thumb: Never trust a money-related request at face value — verify it through a second channel. (e.g., call your bank or the requester directly before sending funds or sharing information).

5. Nearly 1 in 4 mobile devices have a high-risk app installed
According to the Zimperium 2025 Global Mobile Threat Report, about 23% of smartphones have at least one high-risk or “sideloaded” app installed. Sideloaded apps are applications installed on a device from sources other than its official app store. Kaspersky reports blocking about 33 million unwanted mobile software attacks in 2024.
Whether you use an iPhone or Android device, make sure it’s a trusted app before downloading.
Why it matters for you: That free app download could secretly be spying on your data or giving hackers an open door into your phone.
Tips to Prevent Sideloaded / Unwanted App Risks
Turn off “install from unknown sources.” On Android, disable the option that allows apps from outside official stores.
Check the developer’s reputation. Before installing, verify the developer name, number of downloads, and reviews. Avoid apps from unknown publishers.
Review app permissions. Be wary of apps asking for unnecessary access (e.g., flashlight apps requesting contacts or the microphone).
Audit your apps regularly. Delete apps you no longer use. Fewer apps mean fewer potential vulnerabilities.
A good rule of thumb: If you don’t know the source, don’t install the app.

6. Millions of cyberattacks happen daily
NETSCOUT reported more than 8 million DDoS attacks globally in the first half of 2025. The report breaks out more than 3.2 million of those attacks in Europe, the Middle East, and Africa (EMEA). So, the recent data shows that the volume of attacks is far larger than the old “one attack every 39 seconds” stat. That comes from a study by the University of Maryland, and it’s no longer a reliable gauge of today’s scale.
These numbers make it clear: attacks now happen continuously, every second of the day. They’re a constant threat, targeting businesses, organizations, and individuals around the world.
Why it matters for you: Attacks aren’t rare — they’re constant, meaning your personal data is always a potential target if you’re not protected.
Tips to Reduce Cyberattacks
Limit personal information online. Oversharing on social media (location, birthdays, employer details) gives attackers material for spear-phishing or identity theft.
Segment your home/work network. Use a separate Wi-Fi network for smart devices (IoT) so that if one gets compromised, it doesn’t expose your computer or phone.
Be cautious with browser extensions. Only install extensions from trusted developers, and prune them regularly — malicious or abandoned ones are a common entry point.
Log out of accounts on shared or public devices. Don’t leave active sessions open in browsers; always sign out after use.
A good rule of thumb: The less exposed you are online, the fewer doors attackers can open.
7. Connected IoT devices to exceed 40 billion by the end of 2030
According to IoT Analytics, there were 16.6B connected IoT devices at the end of 2023, 18.8B by the end of 2024, and a projected ~40B by 2030. Many 2025 forecasts now sit in the ~20B range. Cybercrime rates are inevitably related to two things: the world population and the number of connected IoT devices. The more people and devices connected to the internet, the more opportunities a hacker has to tap into your personal data.
To elevate your security and your privacy, we strongly encourage you to hide your IP address. Providers, such as Xfinity, include network security that can protect any wired or wireless device in your home connected to the service.
Why it matters for you: Every smart device in your home — from speakers to cameras — is another way hackers can get into your network.
Tips to Protect IoT Devices
Change default usernames and passwords. Never leave factory settings in place — attackers scan for these known defaults.
Disable unnecessary features. Turn off remote access, UPnP (Universal Plug and Play), or voice activation if you don’t need them.
Monitor device activity. Keep an eye on your router logs or use network monitoring tools to detect unusual traffic from IoT devices.
Buy from reputable brands. Choose devices with a history of providing timely security updates and strong privacy practices.
A good rule of thumb: If a device connects to the internet, secure it like a computer.
8. DDoS attacks are estimated to hit 16+ million worldwide by the end of 2025
Netscout has observed over 8 million attacks in the first half of 2025. Cloudflare mitigated 8.5 million in the first half of 2024. It’s reasonable to expect over 16 million attacks by the end of 2025.
A DDoS attack is a malicious attempt to overload a targeted server with massive volumes of web traffic. Typically, these attacks serve two purposes: 1) to slow down or stop your internet connection, and 2) to plant malware on your network.
Some malicious players launch DDOS attacks to disrupt competitors during online gaming matches. Hackers frequently use it to gain unauthorized network access. It’s much easier for hackers to steal personal information like your bank statements or saved passwords once inside.
Why it matters for you: If you’re a gamer or streamer, a DDoS attack could knock you offline or even expose personal data while you play.
Tips to Protect Against DDoS Attacks for Home Users & Gamers
Use a gaming VPN. A VPN hides your real IP address, making it much harder for attackers to flood your connection directly.
Change your IP address. If you suspect you’re being targeted, reboot your modem/router or request a new IP from your ISP.
Don’t share your IP. Avoid posting your IP online, and be cautious when joining unofficial servers, voice chats, or P2P apps that may expose it.
Enable router-level protections. Many modern routers offer built-in firewalls, intrusion detection, or “DoS protection” features you can toggle on.
Use wired connections when possible. A direct Ethernet connection is less prone to disruption and packet loss during traffic spikes than Wi-Fi.
Coordinate with your ISP. ISPs can sometimes detect and block attack traffic before it reaches your home network — ask about DDoS protection services.
A good rule of thumb: Protect your IP address like you protect your gamer tag — if attackers can’t find you, they can’t flood you.
9. 1 in 3 people use a VPN to mask their online connection
A Security.org survey of U.S. consumers in July of 2025 found that about 1 in 3 internet users (32%) currently use a virtual private network (VPN). This is a positive trend we’re happy to report, and it’s a relatively easy step to secure your devices.
A VPN is a privacy tool that masks your online presence, so you can browse online without worrying about snoopers tracking your every move. It essentially hides your IP address by encrypting all data sent and received from your device, making you appear in a different location. This is one of the first lines of cybersecurity defense a user can implement to protect their online data from unwanted eyes.
To find a trustworthy provider, check out these best VPN services
Why it matters for you: Using a VPN helps protect your privacy on public Wi-Fi, keeps your ISP from tracking you, and adds a layer of safety while gaming.
Tips for Using a VPN & How It Helps
Choose servers wisely. For the best speed, connect to servers close to your location. For privacy or bypassing restrictions, pick servers in other regions.
Use reputable VPN providers. Avoid free VPNs that may log or sell your data. Look for services with clear no-log policies and strong security protocols.
A good rule of thumb: If you’re online in public or playing against strangers, connect to a VPN first.
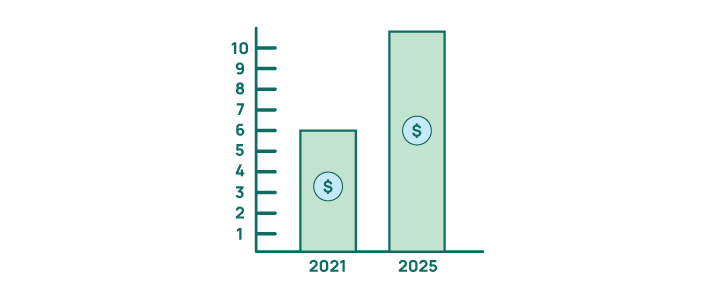
10. Global cybercrime is estimated to cost $10.5 trillion annually by 2025
Cybercrime Ventures estimates it to cost businesses and individuals over $10.5 trillion annually by 2025. You read that right. Trillion. That’s up from $6 trillion in 2021, reports Cybercrime Magazine. It’s more profitable than the combined trade of illegal drugs.
Why it matters for you: That massive figure isn’t just about corporations — it includes the money and data stolen from everyday consumers like you.
Tips to Reduce or Avoid Cybercrime
Use secure payment methods. Stick to credit cards, digital wallets (Apple Pay, Google Pay), or other secure platforms instead of debit cards when shopping online.
Shop only on trusted websites. Look for “https://” in the address bar and avoid deals from unknown sites or random links on social media.
Freeze your credit when not applying for loans. A free credit freeze prevents criminals from opening accounts in your name.
A good rule of thumb: If a deal, message, or request feels urgent or too good to be true, step back and verify — criminals rely on rushed clicks.
Master Cyber Hygiene Checklist
No matter the type of cyber threat — phishing, weak passwords, ransomware, or DDoS — these core practices form your first line of defense.
- Use strong, unique passwords
- At least 12–16 characters, with a mix of letters, numbers, and symbols.
- Never reuse passwords across accounts.
- Enable multi-factor authentication (MFA)
- Add an extra layer of protection, especially for banking, email, and social media accounts.
- Add an extra layer of protection, especially for banking, email, and social media accounts.
- Use a password manager
- Generate and store complex, unique passwords without having to remember them all.
- Generate and store complex, unique passwords without having to remember them all.
- Keep devices and software updated
- Apply patches for operating systems, browsers, apps, and firmware to close security gaps.
- Apply patches for operating systems, browsers, apps, and firmware to close security gaps.
- Secure your home Wi-Fi
- Use WPA2/WPA3 encryption, update router firmware, and change default router passwords.
- Use WPA2/WPA3 encryption, update router firmware, and change default router passwords.
- Encrypt sensitive data
- Use built-in encryption like BitLocker (Windows) or FileVault (macOS) to protect files if devices are stolen.
- Use built-in encryption like BitLocker (Windows) or FileVault (macOS) to protect files if devices are stolen.
- Back up important data
- Maintain both cloud and offline backups to guard against ransomware or accidental loss.
- Maintain both cloud and offline backups to guard against ransomware or accidental loss.
- Be cautious on public Wi-Fi
- Avoid logging into sensitive accounts, or use a VPN to secure your connection.
- Avoid logging into sensitive accounts, or use a VPN to secure your connection.
- Use mobile security software
- Scan for malware and block high-risk apps on smartphones and tablets.
- Scan for malware and block high-risk apps on smartphones and tablets.
- Limit personal information online
- Avoid oversharing on social media — attackers use birthdays, locations, and job details for social engineering.
- Avoid oversharing on social media — attackers use birthdays, locations, and job details for social engineering.
- Turn off unused services
- Disable Bluetooth, NFC, or location sharing when you don’t need them.
- Disable Bluetooth, NFC, or location sharing when you don’t need them.
- Log out of accounts on shared/public devices
- Prevent unauthorized access if someone else uses the device after you.
Stay Smart, Stay Secure
Cybercrime isn’t slowing down — it’s scaling up. From phishing emails and weak passwords to DDoS attacks and vulnerable IoT devices, the threats are everywhere. But here’s the good news: most breaches can be prevented with everyday habits.
By practicing stronger password hygiene, keeping your software and devices updated, being skeptical of suspicious links, and protecting your network with tools like VPNs and encryption, you drastically cut your chances of becoming part of the $10.5 trillion cybercrime statistic.
Cybersecurity isn’t just for businesses or tech experts — it’s for anyone who shops, banks, plays games, or simply browses online. The more proactive you are, the fewer doors you leave open for attackers.
Cybersecurity Facts and Stats FAQs
The top 10 cybersecurity threats include phishing, weak passwords, ransomware, malware, data breaches, DDoS attacks, IoT vulnerabilities, insider threats, social engineering scams, and outdated software exploits. Staying aware of these threats helps users recognize common attack patterns and protect themselves more effectively.
Cyber security facts highlight how everyday habits — like clicking a suspicious link or reusing a password — contribute to most breaches. Knowing the basics empowers users to make smarter online decisions, whether it’s enabling multi-factor authentication, updating software, or avoiding unsafe Wi-Fi networks.
Some eye-opening facts about cybersecurity include: cybercrime costs are expected to exceed $10.5 trillion annually in 2025, about 68% of breaches involve human error, and nearly one in four smartphones has a high-risk app installed. These facts show how widespread cybercrime has become — and why prevention matters.
Home users should know how to:
- Use strong, unique passwords for each account.
- Protect home Wi-Fi with WPA2/WPA3 encryption.
- Avoid oversharing personal info online.
- Back up files to recover from ransomware or hardware failure.
- Consider a VPN for privacy and safer gaming.
Individuals are very much at risk. Attackers often target consumers with phishing scams, identity theft attempts, and financial fraud. In fact, most cyberattacks start with human error — proving that everyday users play a big role in cybersecurity defenses.